Firewalla Purple, 2.5 GbE, and Wi-Fi 6 APs: A late-2021 home + work networking setup that won't break the bank (or your spirit)
I wonder if others share my self-contradiction: while I love learning about new shiny technologies, when it comes to adopting technologies at home, I'm kind of a laggard. Relatively speaking. Which is why it's taken me over 10 years living at my current place to upgrade my home network. I'd like to share my journey to finally taking the plunge. If you're considering something similar, hopefully there's a helpful tidbit or two in here to help you along as well.
The Malaise Era: The "good enough" ISP router solution
In general, I'm absolutely a neophyte: I love learning about and building new things. I'm CTO of a medical device company, my favorite hobby is learning about new software practices and languages, and once, in order to learn microcontroller programming, I created a weight sensor that would count the number of "sessions" my cat had in the litterbox and send me an email when it reached a threshold count (not going to admit what that threshold count was...).
But when it's come to adopting the cutting edge at home, more often than not I find myself waiting unitil someone can polish those sharp edges before adopting them myself. While I'm pretty good at solving tech issues, I'd rather be able to treat my home appliances as appliances, and save my tech support stamina for the day job.

That's why, for home networking, I've always gravitated to a simple "set it and forget it" setup: the standard all-in-one Wi-Fi modem-router-firewall-switch that comes out of the box from the ISP. A couple years ago, I was feeling fancy and added a mesh network to improve coverage out in the yard and in my back office. But still quite vanilla. I was intrigued with trying DD-WRT/Tomato/Open WRT router firmware but didn't really see the cost-benefit of having to maintain it correctly and securely. (This is probably a fallacy - I'm sure there are good examples where I would have been more secure with one of the above than using/trusting my router's commercial firmware. But at least superficially, the default setup seemed like a "solved problem" - why mess with it?)
But recently, I was working on a side-project to set up a Raspberry Pi nature cam in my backyard (more on that someday...), and had to do some "simple" port-forwarding that proved inordinately difficult and confusing. The real issue was hard to pin down—it ended up being somehow related to a "double-NAT" issue between the ISP router, the Google WiFi mesh, and my ISP's DNS (as Scott Hanselman says, "It's always DNS")—but, it took close to a full day to resolve, and ultimately the solution was to turn off the ISP router's DHCP and firewall altogether. This worked, but it was both limiting and unsatisfying, as I had to hang my entire network off the Google Mesh, which is quite bare-bones when it comes to router features and customization.
Based on the above and similar experiences, along with seeing some new products come on the market, I found myself interested to see if I could add faster performance and new capabilities to my network, without breaking the bank, requiring learning major sysadmin skills, or requiring significant routine maintenance.
Requirements
Partitioned network One of the things I really wanted to customize was to partition and monitor my network into different profiles: guest access, general device access, minimal access for IoT devices like the nature cam, and machines I use for work. In particular, it would have been be great to have a partitioned "virtual network" for my work machines that could 1) isolate traffic more securely, to minimize exposure to my company's network when I access office/cloud resources via VPN, and 2) potentially provide a persistent VPN connection to those resources, versus continually having to use software clients for that.
Faster connectivity I also wanted a faster 2.5GbE hard-wired connection and modern Wi-Fi 6 wireless access for my back office (neither of which was available via the Google mesh system), and a firewall VPN that could support the bandwidth of my 1-gigabit internet fiber internet line (I was currently limited to software clients to achieve this, and the connection reliability and performance were surprisingly device dependent).
Network storage Finally, it would be nice to take advantage of a 2.5GbE (or even a minimal 10GbE) "backbone" and have a high-speed local NAS to house local copies of all our valuable data (in addition to their cloud counterparts currently in Dropbox Family and Google Photos). I didn't want to splurge for multi-thousand-dollar commercial solutions for this, but the OSS storage world is becoming quite mature, and the commodity hardware available for DIY solutions are getting very interesting.
Initial Firewall Research: A Goldilocks problem
After researching (read: mostly watching lots of YouTube videos and the occasional Reddit thread—thanks ServeTheHome, Jeff Geerling, NetworkChuck, Lawrence Systems), it seemed like the prevailing wisdom on evolving my firewall/router system was to either go with a "prosumer" Unifi Dream Machine solution, or to run pfSense on my own hardware (Netgate sells pfSense hardware, too, but gigabit-capable VPN appliances get expensive).
Neither exactly fit the bill. On one hand, the Dream Machine was a nice commercial solution, but while Ubiquity has something of a cult following, they tend to have mixed reviews on how they update their products. Also, I didn't need the Wi-Fi of the Dream Machine, since I wanted to have a separate wireless solution (see below). Here's a video showing Network Chuck's infatuation with the thing:
On the other hand, while pfSense seemed quite full featured (and an interesting learning opportunity), I didn't feel like I could "dabble" and still feel like I was creating a reliable and secure appliance that I could learn in a weekend and leave alone for months at a time. And since I needed some decent hardware VPN performance, I couldn't run a simple Raspberry Pi or similar single-board computer solution. Constructing and maintaining a full set of server hardware was going to be both expensive and error-prone (see Lawrence Systems' video explainer on selecting the right hardware and details on virtualization performance for pfSense). Might as well spring for the $699 Netgate 6100 and be done with it...but, ouch that's a bit expensive:
Firewalla Purple: A "just right" user friendly and feature-rich gigabit firewall, router, and VPN
Enter Firewalla, a company that has been innovating to democratize enterprise-level firewall capabilities that are simultaneously affordable and user-friendly. Beyond the great feature set, ease of configuration, and polished mobile software client, the thing that probably impressed me the most was their track record of responding to customer feedback and continuing to evolve their hardware solution to achieve high performance on low-cost SBC platforms. After reading a bit and comparison shopping, I was ready to bite the bullet and purchase their Firewalla Gold for $439. I didn't necessarily need the gigabit switch included in the package, but it seemed to be the right combo of software and hardware features otherwise.
Luckily, I sat on this decision for a minute. Because while I was deciding to commit, they launched Firewalla Purple—a $299 step-down option with everything I needed, and nothing I didn't. Solved.
One of the nice things about Firewalla Purple is that it's very much based on the Gold. And so once any beta software stack issues are resolved, one can expect to have a very similar, full-featured experience as their other products, which tend to have great reviews. I'll be sure to follow-up as things stabilize with any concerns or gotchas I discover.
The Rest
Once I had the firewall "keystone" in place, the rest was downhill. Below, I detail what I used to round out my network. Note: prices are what I paid in July 2021 - as of writing this, the chip shortage has caused current prices to surge higher. I'm using my original prices with the hopes they're more reflective of long-term pricing.
QNAP 10G/2.5G Network Switch
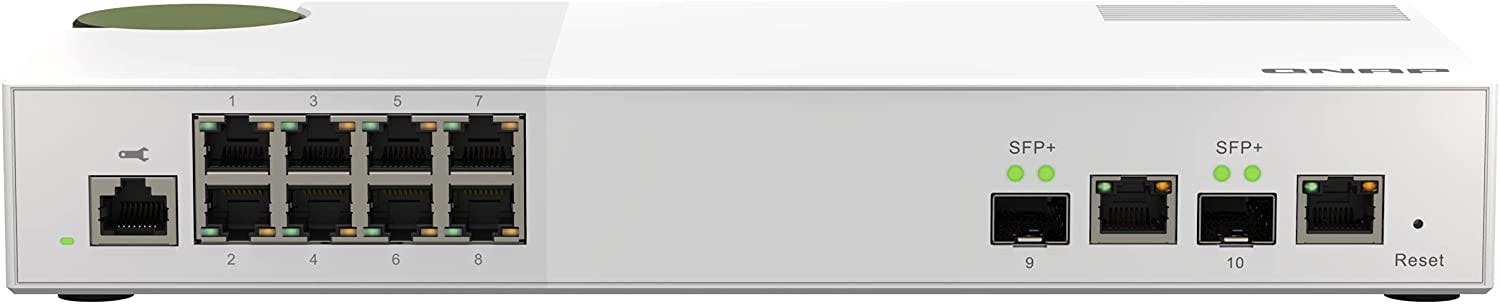
The next piece of the puzzle was the main switch to receive the output of the Firewalla Purple. I ended up splurging on this $339 QNAP QSW-M2108-2C Layer 2 managed switch with 2x10G SFP+/RJ45 combo ports and 8x2.5G ports. This gives me 2.5G for all my downstream devices, a fast 10G "backbone" that I can use to connect my back office to the main house, an additional 10G line that I can use to attach a future DIY NAS, and VLAN capabilities to partition my devices on separate networks as needed.
Netgear 10G/1G Network Switch
For now, I've run a Cat 7 network cable to the back office, so a $199 Netgear GS110MX 10-Port unmanaged switch (8x1G, 2x10G/2.5G) in the back office does the job, allowing my main machine to connect above 1Gbps. This was a compromise in cost, but it's not fantastic value - I feel like the cost of this unit should be $50 cheaper as-is, or add $50 and upgrade the 1G channels to 2.5G. I expect since commodity 2.5G networking is starting to take off, we'll see more affordable options soon.
Unifi WiFi 6 Long-Range Access Points
Two $179 U6-LR-US access points cover our whole property well: one at the center of the house and one for the back office.

Netgear PoE+ 5-port Managed Gigabit Switches
Maybe overkill for just powering the access points (vs buying a PoE injector for each), but these two $49 GS305EP 5-port managed PoE+ switches give me the ability to add other home automation and/or video camera devices in the future. Getting the managed versions will allow me to toggle power to those devices remotely, versus having to physically access the hardware.

Sabrent 2.5Gbps USB-C adapters
For a surprisingly-affordable $35, Sabrent NT-S25G USB-C to 2.5GbE adapters are quick and quiet. Assuming they continue to prove reliable, they will be my go-to for most systems. (Sabrent also offer a 10G Thunderbolt 3 option for $160, for those machines without a PCI-E NIC option)

Wrapping up
At the end of the day, I now have a brand new managed 10G/2.5G + Wi-Fi 6 home networking setup with a sophisticated and user-friendly firewall, PoE+ smart device expansion options, and room for a high-performance DIY home NAS upgrade, all for the price of an entry-level MacBook Pro. Pretty happy with the value here. As a caveat, I'm definitely still in the honeymoon period, so I'll be sure to update as things progress.
Hope this walk-through was helpful! What hardware/software combos do you use? I'd be very interested in hearing from other people's expertise and experiences down in the comments below.
Thanks for reading, and talk soon. David